macOS 10.15.4 shows message that a “Legacy System Extension” will be incompatible with a future version of macOS.
- Why Does Little Snitch Think My Ip Is In Kansas State
- Why Does Little Snitch Think My Ip Is In Kansas Right Now
- Why Does Little Snitch Think My Ip Is In Kansas 2017
- Why Does Little Snitch Think My Ip Is In Kansas Lyrics
- Why Does Little Snitch Think My Ip Is In Kansas Today
- Why Does Little Snitch Think My Ip Is In Kansas City
Jan 15, 2012 I think someone is trying to connect to my computer, or my network, something. Little Snitch alerted me that an ip address was trying to connect. I denied it, obviously. It is not an ip that I know of, as it certainly isn't mine. How can an ip address connect to my computer and why? The ip address seems to belong to 'Total Server Solutions LLC,' a type of business.
Why Does Little Snitch Think My Ip Is In Kansas State
Starting with macOS 10.15.4 the above “Legacy System Extension” message will be shown when Little Snitch is installed.

→ Please read this blog post to learn more about why this message is shown.
Why Does Little Snitch Think My Ip Is In Kansas Right Now
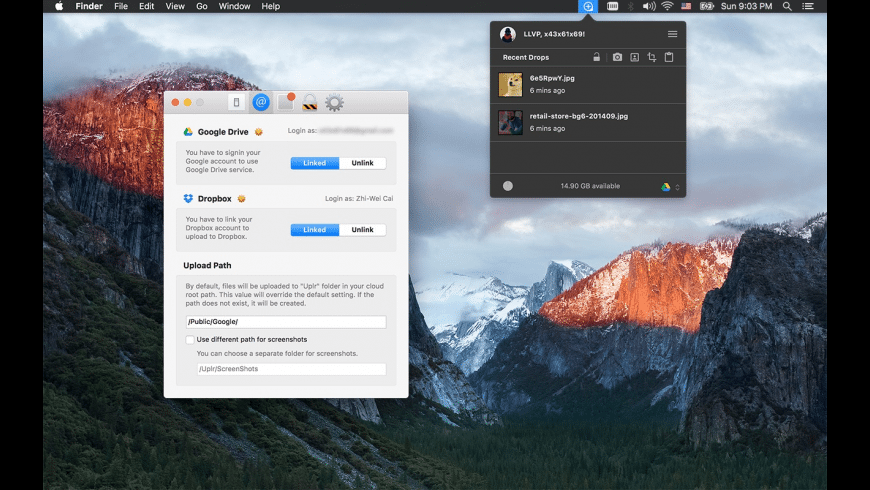
Why Does Little Snitch Think My Ip Is In Kansas 2017
Will there be an update of Little Snitch that’s compatible with macOS 10.16?
Yes. We are going to release Little Snitch 5 later this year, which will be compatible with macOS 10.16. → Learn more…
Why Does Little Snitch Think My Ip Is In Kansas Lyrics
Will I get the update for free?
Yes. All licenses sold now include a free upgrade to Little Snitch 5. In addition, customers who purchased Little Snitch 4 within a one-year period prior to the final release of Little Snitch 5 will also get a free upgrade. → Learn more…
Why Does Little Snitch Think My Ip Is In Kansas Today
Will Little Snitch 4 run on macOS 10.16?
Little Snitch 4 will not be loaded on macOS 10.16 by default, but there will still be an option to allow the loading. → Learn more…
Why Does Little Snitch Think My Ip Is In Kansas City
As Tinkster pointed out the first step is to take the machine off line. It is best to do this by either disconnecting the network cable or putting up a firewall (iptables) to only allow SSH connections from a trusted source. Once you have secured the machine you can work with much less possibility of interference. The next step would be to review the CERT intruder detection checklist. It will give you an overview of the investigation process. Don't worry if a lot of it doesn't make sense, we can help with that.
Now, to begin, would you please describe what is happening that leads you to suspect that your machine may have been compromised? Please provide as much specific detail as possible, including log entries if you have them.